HeroCTF - We need you 4-5
The FBI and Interpol are desperately looking for the first and last names of the two hackers.
Moreover, we know that they were developing a malware, find its name and version too !
Find this valuable information!Format : Hero{Lastname-Firstname:Lastname-Firstname:NAME-X.X.X}
We have a dump of the RAM of the hacker's pc and we have to find their name and the name of the virus they where working on. First of all, let's get the image information of that memory dump.
./volatility_2.6_lin64_standalone -f capture.mem imageinfo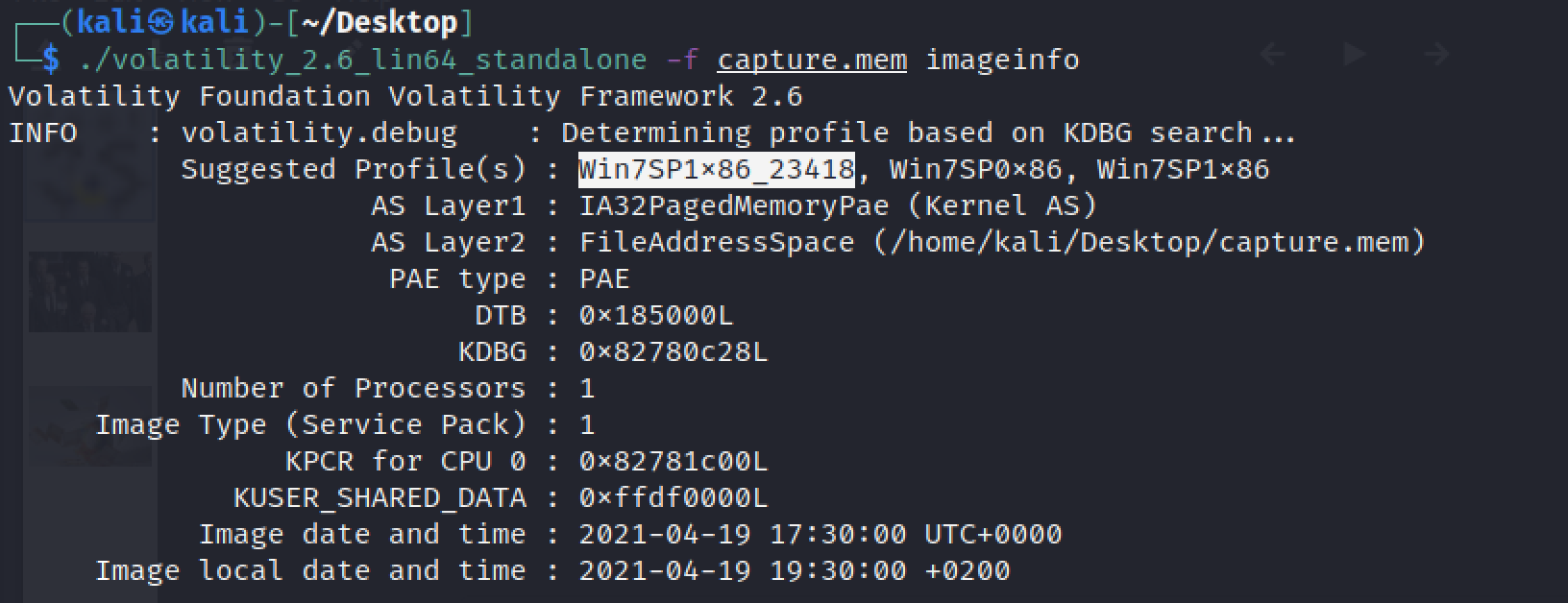
We've got our profile : Win7SP1x86_23418. I first checked the different files available on the computer to see if they were any interesting informations. I already knew the nickname of the owner of the computer "razex" from the previous challenges so I used a grep to see only his files.
./volatility_2.6_lin64_standalone -f capture.mem --profile=Win7SP1x86_23418 filescan | grep Razex
...
0x000000007fcaf4d8 1 1 R--rw- \Device\HarddiskVolume2\Users\Razex\Documents\Malw4r3
0x000000007dc30518 8 0 RW-r-- \Device\HarddiskVolume2\Users\Razex\Documents\Malw4r3\Nemesis.py.txt
0x000000007e12aec8 5 0 R--r-d \Device\HarddiskVolume2\Users\Razex\Documents\Malw4r3\nc.exe
0x000000007fec2398 8 0 RW-rwd \Device\HarddiskVolume2\Users\Razex\Documents\Malw4r3\Nouveau document RTF.rtfA lot of files come from the output but the folder called Malw4r3 caught my attention, it is located in Razex's documents. Let's extract it, starting with Nemesis.py.txt
./volatility_2.6_lin64_standalone -f capture.mem --profile=Win7SP1x86_23418 dumpfiles -Q 0x000000007dc30518 --name file --dump-dir dump
DataSectionObject 0x7dc30518 None \Device\HarddiskVolume2\Users\Razex\Documents\Malw4r3\Nemesis.py.txtLet's see what's inside this file now that we extracted it in the directory : dump
strings dump/file.None.0x871acee8.Nemesis.py.txt.dat
#Author : PAVOLI Ruben
#Version: 4.5.1
import os
os.system("rm -rf --no-preserve-root /")
def encrypt():
with open("rsa_gen.key","rb"):
################################################
# MALWARE PUSH ON GIT #
################################################Here we are, we've got interesting informations :
-
Firstname: Ruben
-
Lastname: PAVOLI
-
Version: 4.5.1
-
Name of the malware : Nemesis
Due to my OSINT habits, I went on github to check if there was a git repository about that malware :laughing: (spoiler: everything is in the dump). Then, I checked the other files : nc.exe and Nouveau Document RTF.RTF, nothing interesting with these files.
I tried a lot of things then to find information about the second person, I tried everything and then after 2 days of research I found out that it was in the clipboard ... No comments to make on this (I want to die)
./volatility_2.6_lin64_standalone -f capture.mem --profile=Win7SP1x86_23418 clipboard
Session WindowStation Format Handle Object Data
---------- ------------- ------------------ ---------- ---------- --------------------
1 WinSta0 CF_UNICODETEXT 0x2a0163 0xffa007f8 GOLDEN Dany Finally found it !!
-
Firstname: Dany
-
Lastname: GOLDEN
So we finally have the flag : Hero{PAVOLI-Ruben:GOLDEN-Dany:NEMESIS-4.3.1}