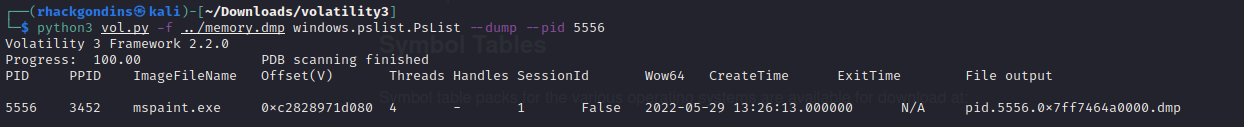
Computer analysis 1/3
We finally got access to the computer of one of these criminals that we were looking for. Help us to investigate that case !
First we need to identify his computer, find his computer name
Flag : ETCF{computername}We can solve this first part with a simple command and using volatility3 python3 vol.py -f ../memory.dmp windows.envars.Envars | grep COMPUTERNAME
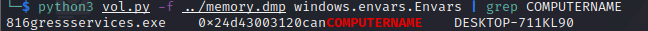
Flag: ECTF{DESKTOP-711KL90}
Computer analysis 2/3
It looks like he was infected by a malware, we needs more information about it.
ECTF{serverip:port-malwarename:PID}By running a python3 vol.py -f ../memory.dmp windows.netscan.NetScan we can see a foreign adress for ctfmon.exe that is unusual and a strange port as well. Ctfmon.exe is supposed to be used by Microsoft to controle the user input text and the MS office language bar normally, it's not supposed to be connected to a remote server.
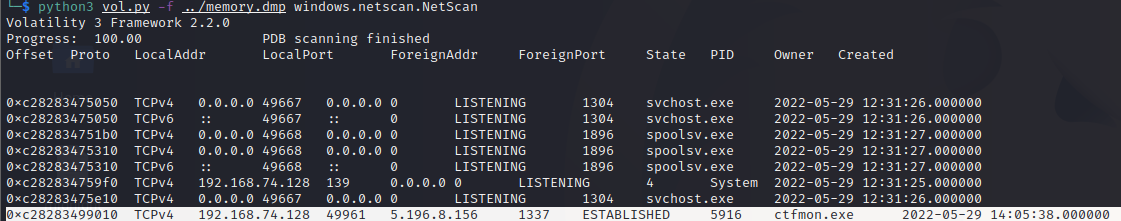
We can now extract the ip of the remote server, the port, the PID and the program name. If we are not sure, we can also look at the command user by the user and we clearly see two times that ctfmon.exe were run.
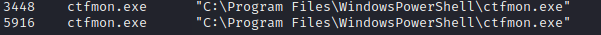
Flag ECTF{5.196.8.156:1337-ctfmon.exe:5916}
Computer analysis 3/3
Bravo, now we need to know what this person was doing on his computer when the malware executed, he probably left a message!
ECTF{}First we can dump the process, here I used the PID of Paint but it works with any other.
Now, by changing the extension to .data we can open it using GIMP to visualize the desktop of the user
Here is our flag : ECTF{W3LL_D0N3_SH3RL0CK}